Facial Authentication The Future of Secure and Intelligent Digital Access
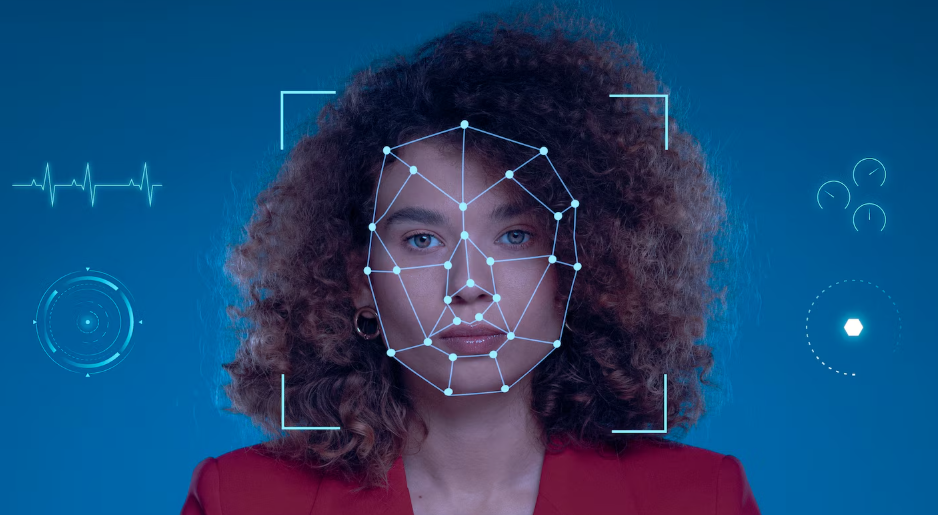
In a world where digital security is more critical than ever, Facial Authentication has emerged as a reliable, fast, and user-friendly solution for identity verification. From unlocking devices to securing enterprise systems, this advanced biometric technology is transforming how businesses and individuals protect sensitive data. As cyber threats increase, organizations are rapidly adopting facial recognition systems to ensure accuracy, efficiency, and trust in digital interactions.
What Is Facial Authentication and How Does It Work?
Facial Authentication is a biometric security method that verifies a person’s identity by analyzing unique facial features. Unlike passwords or PINs, it relies on physical characteristics that are difficult to replicate.
The process typically involves:
-
Capturing a facial image using a camera
-
Mapping facial landmarks such as eyes, nose, and jawline
-
Converting the data into a mathematical facial template
-
Matching it against stored biometric data for authentication
This contactless authentication method enhances security while delivering a seamless user experience.
Key Benefits of Facial Authentication Technology
Businesses across industries are adopting Facial Authentication due to its wide-ranging advantages:
-
Enhanced security: Revenue Cycle Management Services Reduces risks associated with stolen passwords or credentials
-
Fast verification: Enables real-time identity verification within seconds
-
User convenience: Eliminates the need to remember complex passwords
-
Scalability: Easily integrates with cloud-based systems and enterprise tools
-
Fraud prevention: Detects unauthorized access and identity spoofing attempts
These benefits make facial recognition software ideal for both consumer-facing and enterprise environments.
Facial Authentication vs Traditional Security Methods
Compared to conventional security solutions, Facial Authentication offers superior reliability and efficiency.
Traditional methods limitations:
-
Passwords can be forgotten, shared, or hacked
-
ID cards can be lost or duplicated
-
PINs are vulnerable to brute-force attacks
Facial Authentication advantages:
-
Uses unique biometric data
-
Harder to forge or steal
-
Provides frictionless access control
This makes it a preferred choice for modern access management systems and secure digital workplaces.
Use Cases Across Industries
Facial Authentication is being widely implemented across multiple sectors:
-
IT & Remote Work: Secure logins for distributed teams and device access
-
Healthcare: Protecting patient records and supporting
-
Finance: Fraud detection, KYC compliance, and secure transactions
-
Corporate Security: Attendance tracking and workplace access control
-
Digital Forensics: Supporting tools like eInvestigator for identity validation
Its adaptability ensures both security compliance and operational efficiency.
Privacy, Compliance, and Ethical Considerations
While Facial Authentication offers advanced security, responsible implementation is essential. Organizations must address:
-
Data encryption and secure storage
-
User consent and transparency
-
Compliance with global data protection regulations
-
Ethical use of facial recognition technology
By following best practices, businesses can balance innovation with privacy protection.
The Role of Facial Authentication in Modern Work Environments
As remote and hybrid work models grow, Facial Authentication plays a crucial role in securing digital endpoints. It ensures that only authorized users access systems, reducing insider threats and credential misuse. When combined with AI-powered monitoring and analytics, it creates a robust security ecosystem for modern enterprises.
Conclusion: Secure Your Business with Facial Authentication
Facial Authentication is no longer a futuristic concept—it’s a practical, proven solution for organizations seeking secure, efficient, and user-friendly identity verification. Whether you’re managing remote teams, protecting sensitive healthcare data, or strengthening enterprise security, facial recognition technology offers unmatched value.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Игры
- Gardening
- Health
- Главная
- Literature
- Music
- Networking
- Другое
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness


